How to setup NTLM authentication with SQLMap using Burp suite's proxy feature
So I wanted to test a database against SQL injection with SQLMap, but it was
secured with NTLM authentication. I ran into a [CRITICAL] sqlmap requires
Python NTLM third-party library in order to authenticate via NTLM. Download
from 'https://github.com/mullender/python-ntlm' error before I figured out
what to do.
Last update:
Time to read: less than a minute.
Running the command sqlmap -u https://<ip_address>/<api_endpoint>/?param= --level=5 --auth-type=NTLM --auth-cred=<windows_machine_name>\<ntlm_username>:<ntlm_password> produced the following error:
[CRITICAL] sqlmap requires Python NTLM third-party library in order to authenticate via NTLM. Download from 'https://github.com/mullender/python-ntlm'
No worries, just install python-ntlm using Pip: pip install python-ntlm. After running the SQLMap command again, another error informed me that the python-ntlm package uses Python 2’s syntax:
[CRITICAL] wrong initialization of 'python-ntlm' detected (using Python2 syntax)
Python 2 is considered deprecated since about the Stone Age, so naturally, I tried installing the version ported to Python 3:
pip install python-ntlm3
This resulted in the same error message as before, so I figured that SQLMap
probably can’t use the python3-ntlm package yet due to lack of an
implementation. I had to search for an alternative method to authenticate using
NTLM.
Luckily, a blog post from 2014(!) informed me to try using Burp Suite as a proxy, so that every attack payload SQLMap sends is routed through the proxy that handles the NTLM authentication first before reaching the database server. I tried just that.
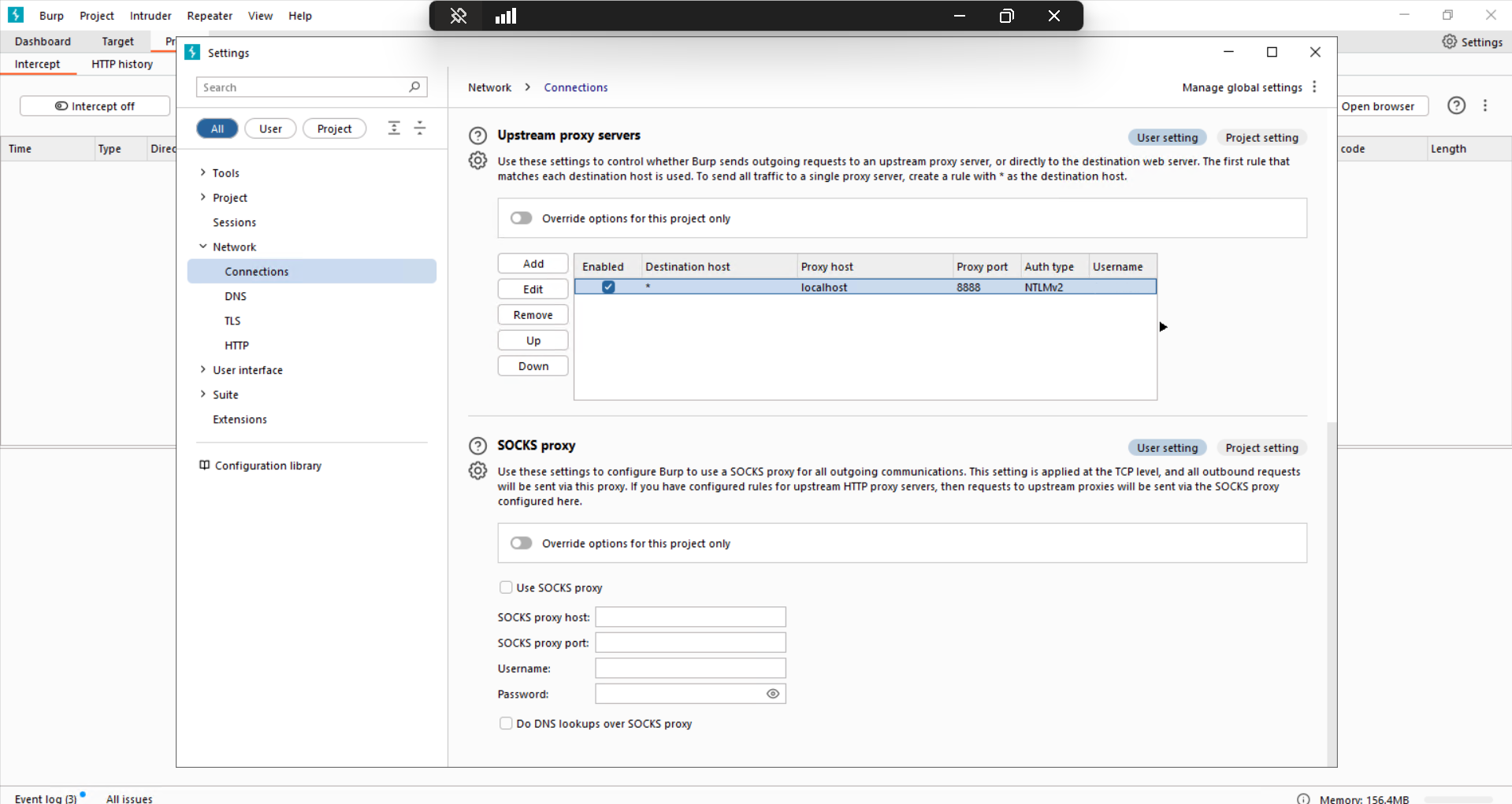
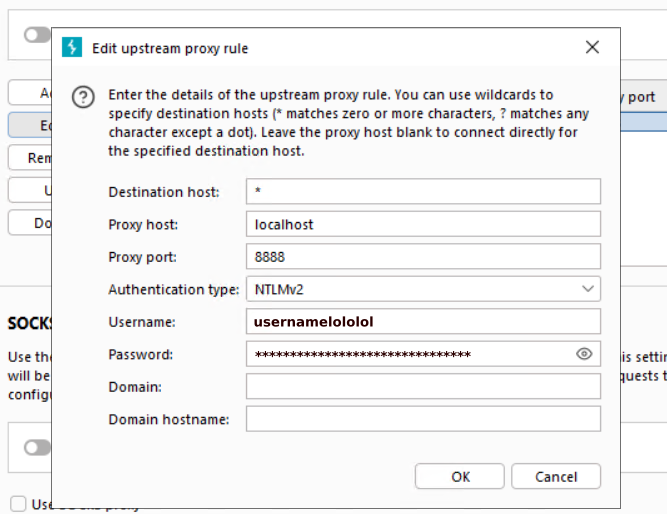
So yeah, after setting everything up in the Settings -> Network -> Connections -> Upstream proxy servers menu (I input port 8888 here, while Burp runs on port
8080, authentication is NTLMv2 and I supplied the NTLM username and password),
and routing SQLMap through this proxy, the scanning started, so I could
successfully scan the database for SQLi vulnerabilities. The final SQLMap
command looked like this:
sqlmap -u https://<ip_address>/<api_endpoint>/?param= --proxy https://127.0.0.1:8080 --level=5
If you have any comments, you can add them under this post of mine on Fedi/Mastodon: https://mastodon.grin.hu/@BeanieBarrow/114132356852906893.